What Is Phishing?
Phishing is a cyber-attack where criminals impersonate trusted sources or people you may know to trick you into revealing sensitive information or taking harmful actions.
How to Identify Phishing
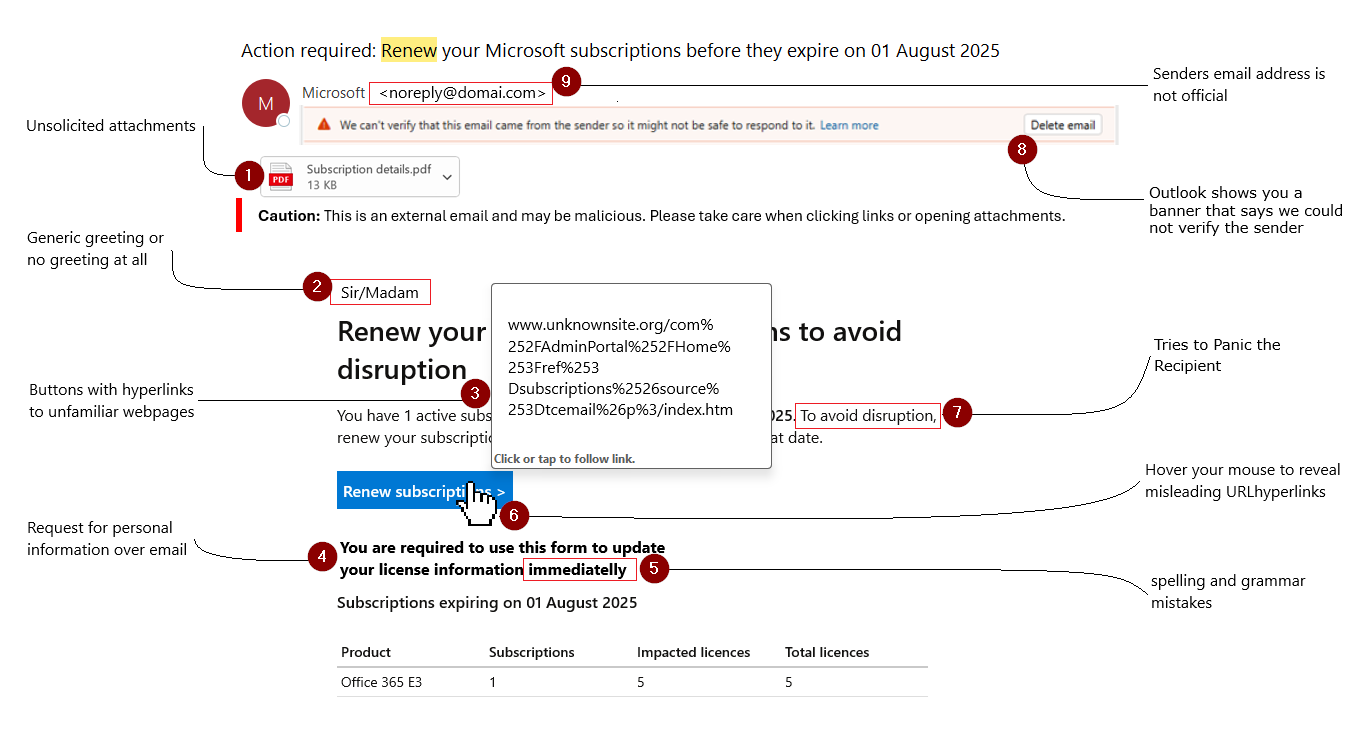
- Includes Unsolicited Attachments (The file name and message may be crafted to spark curiosity or urgency—like “Urgent_Payment.pdf” or “Resume_John.docx”)
- Is Not Personalized. Use generic greeting or no greeting at all
- Contains redirecting link or buttons to unfamiliar websites (e.g., “Verify Now”, “Click here”, or “Download Invoice” but actually redirects to a fake one (
phishingsite.com) - Asks for Sensitive or Personal Information (Password, PIN, or Account Verification Code)
- Uses Poor Spelling and Grammar
- Contains Links that Don’t Match the Domain (e.g.,
secure-paypal.comorpaypal.verify-login.netthat mimic legitimate sites) - Tries to Panic the Recipient (Phrases like “Your account will be suspended,” “Immediate action required,” or “Security breach detected,” Time sensitive.)
- Outlook shows you a banner that says we could not verify the sender
- Uses an unknown or different domain (e.g., jsmith@micros0ft-support.com)
How to Prevent Phishing
- Think before you click any link or buttons: Hover over links to inspect URLs even from known contacts—verify first.
- Verify attachments. Inspect the file type
- Common Dangerous File Types
.exe,.bat,.scr: Executable files that run malicious code..doc,.xls,.ppt: Office files with embedded macros..zip,.rar: Compressed files that hide malware inside..pdf: Can contain scripts or links to phishing sites.

- Common Dangerous File Types
- Verify requests if the email came from your organization: Contact the person via trusted methods—not by replying directly on the suspicious email
- Report suspicious activity: Don’t ignore your instincts (Unusual or repetitive urgent request)
- Keep software up to date: Security patches help block known vulnerabilities
- Have a secure password: Use a mix of uppercase, lowercase, numbers, and symbols
- Confirm that you have multifactor authentication
What to Do If You Suspect Phishing
- Do NOT respond, click, or download anything
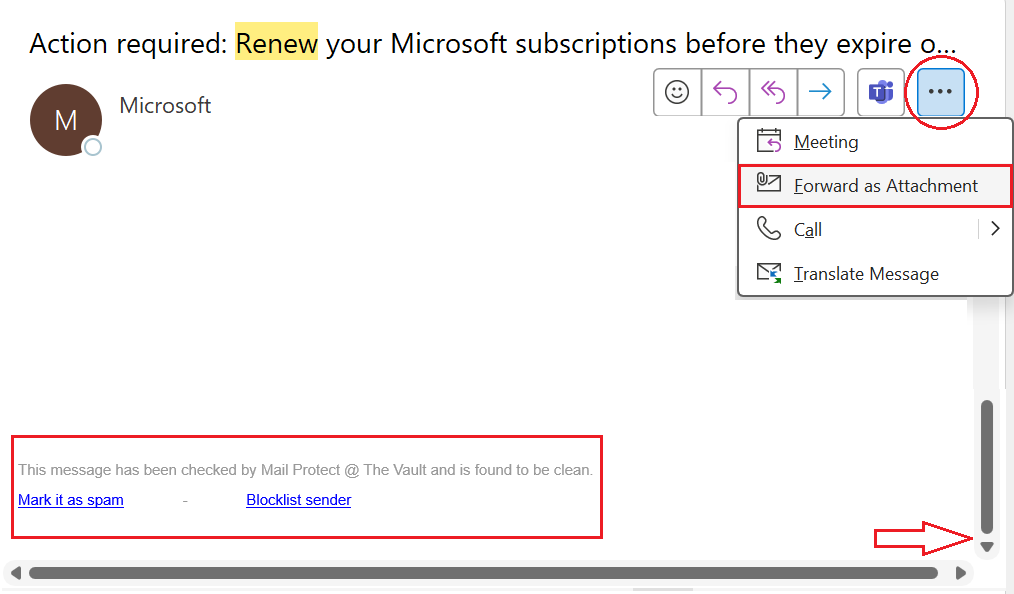
- Report the email. Forward as an attachment to help@igd.com.au
- Review email footer. You can block or marked email as spam (This feature may not be available for non-mail protect customers)

- Delete the message if confirmed suspicious
- Follow up if you clicked or shared information: Contact IT immediately
If you’re suspicious that you may have inadvertently fallen for a phishing attack, there are a few things you should do.
- Write down as many details of the attack as you can recall. Note any information such as usernames, account numbers, or passwords you may have shared, and where the attack happened such as in Teams, or Outlook.
- Immediately change the passwords on all affected accounts, and anywhere else you might use the same password.
- Confirm that you have active multifactor authentication (also known as two-step verification) turned on for your account.
- Notify the IT support at your work or school of the possible attack.
- If you shared information about your credit cards or bank accounts, you may want to contact those companies as well to alert them to possible fraud.
- If you’ve lost money, or been the victim of identity theft, don’t hesitate, report it to local law enforcement. The details in step 1 will be very helpful to them.